Research by a security company, ForeScout, has demonstrated how hackers can use malware to compromise building automation systems (BAS). The company did this by developing and testing a proof of concept (PoC) malware that successfully exploits two critical bugs in the BAS programmable logic controllers (PLCs).
The bugs are in the PLCs as well as in the gateway protocols of the building automation systems. Their PoC malware specifically targets the surveillance, access control systems, HVAC and other technologies in the modern-day smart building as well as industrial control systems (ICS). In addition to the two vulnerabilities, PoC malware can exploit several other flaws in the building automation systems.
Using rogue malware, attackers can exploit the flaws and launch attacks that range from cross-site scripting (XSS) and arbitrary file detection to authentication pass and path traversal.
Risks of vulnerabilities in building automation systems
Attacks on building automation systems can lead to dangerous situations. For example, the attackers can exploit the flaws to compromise the physical access control system and gain unauthorized entry, or the HVAC devices and causes overheating of data center equipment.
Considering the wide range of the BAS components and networks, the flaws present a very dangerous scenario. Other than the HVAC and access control systems, the vulnerabilities affect an extensive network of the critical parts, including energy production units, fire alarms, elevators, video surveillance and more. Generally, it affects the entire infrastructure that is part of almost all buildings in hospitals, schools, airports, stadiums, data centers and more.
Ways to compromise building automation systems
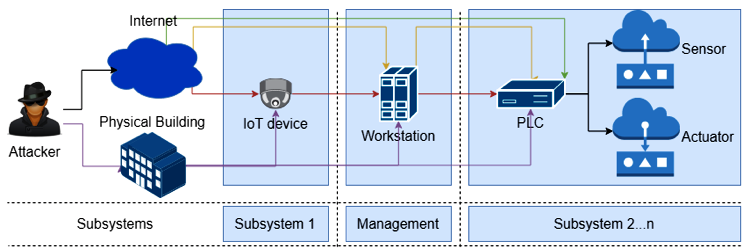
According to the research, test malware has the ability to attack the building automation systems in the following ways;
- Penetrate the network and access the PLCs after gaining physical access into an air gap network
- Exploit vulnerabilities in the publicly accessible PLCs that control or activate the sensors and actuators
- Compromise publicly accessible IoT devices such as IP cameras and routers hence gain access to the network and connected systems.
- Expose the computers that manage the building automation system hence allow the attackers to access the PLCs.
Data from some major device search engines, the Shodan and Censys, that identifies internet-connected computer hardware shows that thousands of devices are vulnerable to these security flaws. In addition, the ForeScout researchers add that the BAS attach surface is rapidly expanding, especially due to the excessive integration of IoT devices into the building automation systems.
So far, most of the companies that manufacture automation devices such as the PLCs have addressed the vulnerabilities by releasing patches. However, the research shows that attackers can find and exploit other unknown vulnerabilities that allow them to penetrate and compromise building automation systems. As such, manufacturers should continuously monitor, test, and address security issues on their products.
Security issues in smart TVs
Besides the building automation systems, other internet-connected devices such as smart TVs are also vulnerable to malware. Generally, since these are like small computers that rely on the internet, the apps and operating systems such as Android TV, WebOS, Tizen, OperaOS, and others have security flaws and vulnerabilities that expose them to a wide range of cyberattacks. On the other hand, cable TV is more secure since it relies on a dedicated connection less exposed than the public internet.
Despite the security risks, automation and smart devices provide some comfort, flexibility, optimization, cost-benefit, and ease of doing things. For example, many people are “cutting the cord” after they compare cable costs with streaming services! Switching to smart or connected TVs allows them to stream a wide range of shows through the internet, and in a more flexible way.
As digital technology advances, manufacturers, and third-party providers are working on ways to address most of the security issues. However, even the consumers should take precautions to remain secure when using connected devices.