The world is becoming more and more complex. Businesses, people, and data are everywhere. Attack surfaces are expanding every day, and internal threats remain an issue that requires constant attention. On top of that, security forces are faced with billions of alerts and countless false positives that distract their already limited resources from responding to real threats.
Yesterday’s security solutions cannot provide complete protection. CISO and their teams already know that it is impossible to guarantee protection with legacy tools, which typically:
- remain ineffective, providing a certain functionality, but not the desired results – the same old tools of ten years ago have long been calculated by cybercriminals.
- not equipped with credential threat detection – “More than 80% of breaches are due to brute force or lost/stolen credentials” (Verizon 2020 Data Breach Investigation Report).
- create the burden of having to manually investigate every false positive – this is 33% of all alerts in traditional SIEM (Ponemon Institute study).
- take 74% of analysts’ time.
In fact, security forces are constantly trying to catch up. Focusing on what has already happened can lead them to lose sight of what is happening at the moment. And they won’t be able to identify potential security issues that will go unnoticed in the future.
Security teams need a modern and reliable approach that is as lightning-fast and tough as the adversaries they face. Exabeam solutions were designed from the ground up to adapt to an ever-changing environment. And they help CISO bypass many of the tricks by adding intelligence to existing security tools, including Security Information and Event Management (SIEM), Extended Detection and Response (XDR), Cloud Data Lake, and hundreds of other business and security products.
Behavioral analytics, end-to-end automation, and prescriptive content can give professionals the tools and techniques they need to confront attackers and the complexity of ubiquitous threats.
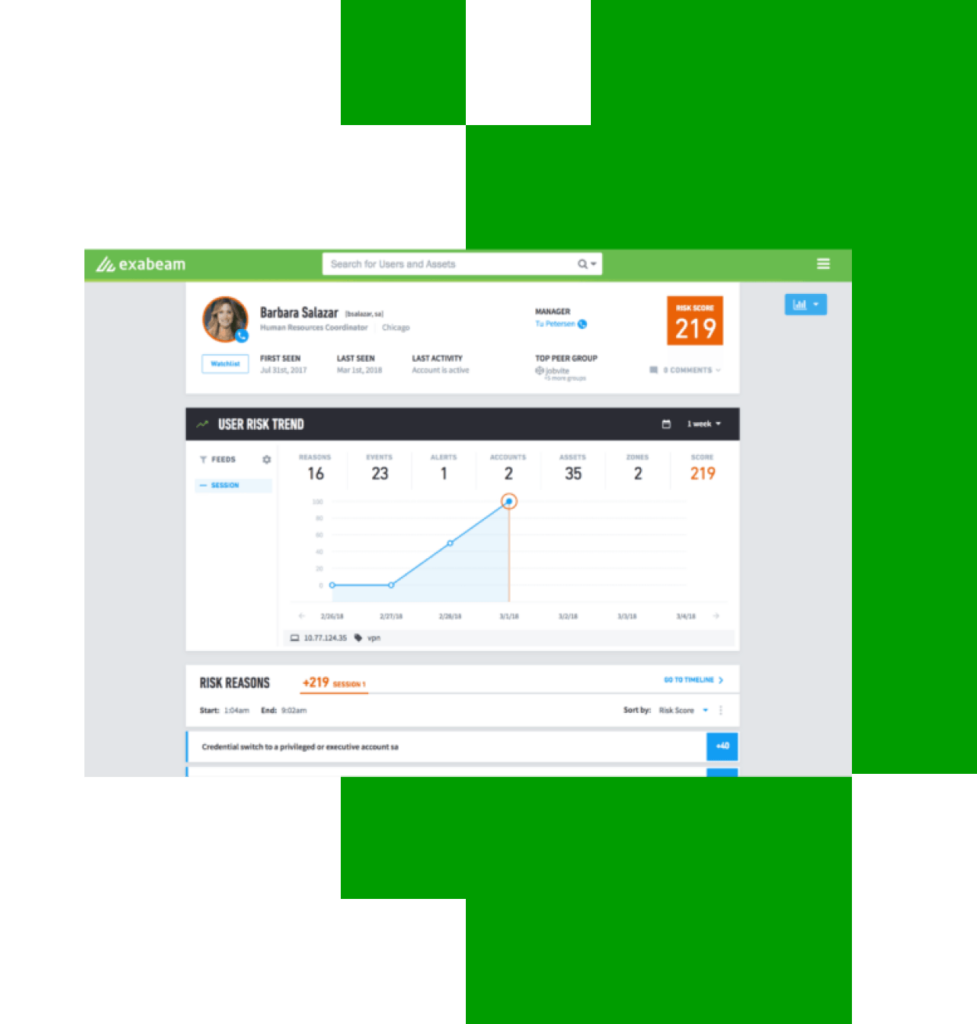
If an attacker steals or otherwise obtains user credentials, or if an insider is the source of the attack, they enter the network rather than hacking into it. This type of access will not be considered an attack. Subsequent actions of such attackers can also bypass detection tools if the attack mimics normal user activity. Exabeam tools enable analysts to quickly identify compromised insiders or employees with a destructive intent that were previously difficult, if not impossible, to find.
Exabeam provides a continuous display of real-time logs to correctly correlate all activities and behaviors with users as well as devices. This attribution, combined with data enhancement and additional context, enables unusual employee behavior to be detected. Especially if they are accessing data and devices that are not normally used, or if they are logging in using a different user ID, or when they are trying to give themselves more administrator privileges.
Speed is the primary metric by which analysts are measured, especially their mean time to response (MTTR) to incidents. This is true whether the analysts are part of the general security team or the insider threat team. However, before responding to an incident, they must first detect and process alerts to determine which ones are worth considering and which are false. And then analysts must conduct research on potential incidents to understand the scale of the attack.
IS teams can address labor shortages by automating repetitive tasks as well as those that have to be done manually. This automation can improve the efficiency of the entire workflow – from collection and detection to response. And this is especially important at a time when there is an acute shortage of time.
Exabeam customers estimate that their spending on tasks can be reduced by 51% using these funds. At the same time, almost 90% of customers believe that the operational costs of detection and investigation are also reduced. In particular, analysts spend less time processing false positives. About 85% of customers report Exabeam to be effective in reducing false positives.
Security teams also mitigate risk by improving visibility. Many analysts using Exabeam products claim they can handle significantly more alerts: 83% of daily alerts versus 45% with other SIEM solutions.
Each type of attack is a specific issue that requires the IS group to have transparency in all processes, clear detection logic, and incident investigation and response procedures. Their ability to engage a particular use case depends on the capabilities of the technology, as well as on the availability of a description for that use case and on the ability of specialists to adapt the solution to their environment.
Exabeam use cases enable cybersecurity departments to achieve consistent success and, over time, improve their effectiveness against attacks involving compromised insiders and outside threats. Ready-to-use content dramatically simplifies analyst workflows from data collection to detection, investigation, and response. To make it easier to get started, organizations are provided with clear guidance on the data sources they need to deploy. Along with this, detection models contain descriptions of specific tactics and methods of the enemy, and they are compared with the structure of MITER ATT & CK. The tailored individual lists can then be customized so that analysts can track high-risk users and devices.